A new security vulnerability has been disclosed before a patch has been made available. It’s a “remote code execution” bug which means that an attacker can use it to effectively take over vulnerable computers. It exploits the compression features of the the common windows file sharing protocol SMB
Many enterprises will rely on file sharing and cannot simply turn off SMB, but they can switch off support for the compression features. This will prevent an attacker from being able to use a file share on a machine as a means of taking over that machine. It will not however prevent them from setting up a file share and that would attack any machine that connected to it: potentially a new form of phishing attack. Users should be reminded to never click on links or open attachments that they weren’t specifically expecting.
To roll out the mitigation in an enterprise we can use group policy preferences to apply a registry change.
We need create or update a registry DWORD called DisableCompression in the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters\ registry key.
This can be achieved from a suitable Group Policy Object by creating a new Registry entry under Computer Configuration | Preferences | Windows Settings | Registry using the Replace Action as below
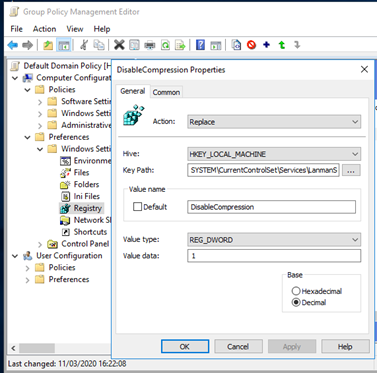
DisableCompression = 1