Not too long ago I listened to a podcast that mentioned the “Interplanetary file system” in the context of the self sovereign internet
That was the first time I’d heard of IPFS but I didn’t really learn anything much about it. It was an aside in a fascinating and wide ranging discussion.
However it did mean that it rang a bell with me when I read about an announcement today. This was regarding Brave launching support for IPFS in the new version 19.
I already use the Brave browser so why not see how easy or difficult it is to get going.
First thing to do was check my version and update. A simple matter of clicking on the menu button and choosing About Brave
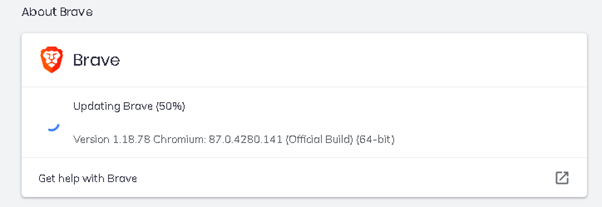
A minute or two later and I click relaunch to ger the new version. Now to see what I can access.
The article links to a mention of an unblockable copy of wikipedia which in turn links to https://ipfs.io/ipfs/QmXoypizjW3WknFiJnKLwHCnL72vedxjQkDDP1mXWo6uco/wiki/
However that’s an https link. I tried it on another PC where I hadn’t updated and confirmed I could access that without a problem. But with the article’s mention of an ipfs:// prefix the obvious thing to try is editing the url to
ipfs://QmXoypizjW3WknFiJnKLwHCnL72vedxjQkDDP1mXWo6uco/wiki/
Bingo!
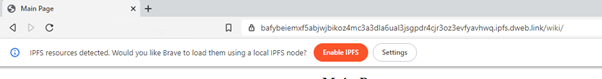
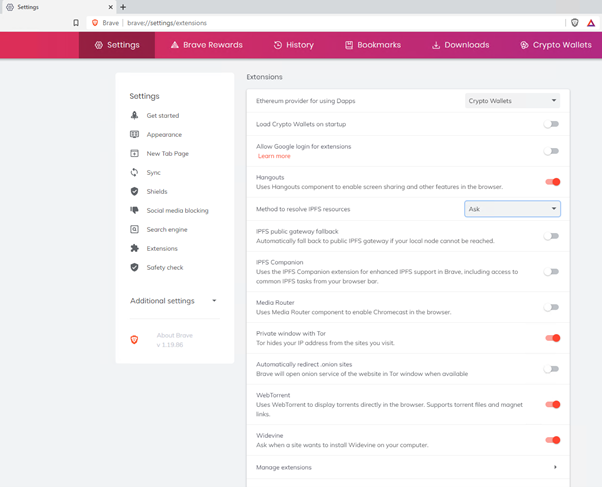
A quick look at those settings before I click enable.
And then after enabling I get the following message from Windows Defender Firewall
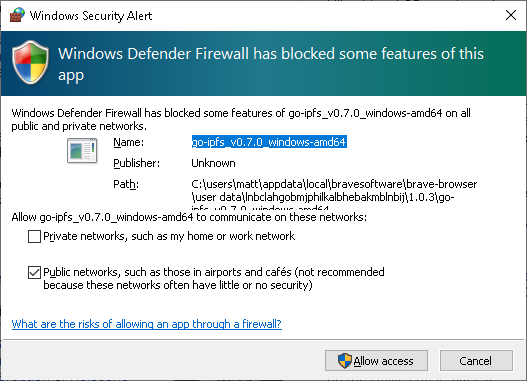
I allow access and away we go.
I checked back on those settings. Clicking enable had simply changed the “Method to resolve IPFS resources from “ask” to “Local Node”
There’s no search feature but by using the regular wikipedia site for reference I was able to figure out the url to a page that wouldn’t usually be allowed on the other side of the great firewall of china.
Certainly, this is easy enough. Of course what’s a boon for liberty is a curse for the network security administrator. Time to figure out this new magic and check with our vendors how much this might bypass our regular monitoring and filtering.